Allied Cybersecurity - Blogs
The clock is ticking! As of December 15th, 2023, the new cyber incident reporting rules set forth by the Securities and Exchange Commission (SEC) are officially in effect. These updated regulations significantly impact how publicly traded companies must disclose cybersecurity incidents, and unprepared organizations face potentially hefty fines and reputational damage. What's new in the reporting landscape? Expanded scope: The definition of a reportable incident has broadened, requiring disclosure of events that may not have been considered material under previous guidelines. This includes ransomware attacks, data breaches affecting non-public data, and even near-misses that could have led to significant harm. Tightened deadlines: Companies must now report material cybersecurity incidents within four business days of determining their materiality. This compressed timeframe demands swift and accurate incident investigation and response procedures. Enhanced transparency: The SEC is requiring more detailed and structured reporting, including information on the nature of the incident, its impact on the company, and the remedial actions taken. This increased transparency aims to provide investors with a clearer picture of a company's cybersecurity posture and risk management practices. Why should you care? Even if your company isn't publicly traded, staying informed about these new regulations is crucial for several reasons: The expanding cyber threat landscape: Cyberattacks are becoming increasingly sophisticated and frequent, impacting organizations of all sizes across all industries. Understanding the reporting requirements can help you prepare even if you're not currently subject to them. Potential reputational damage: A data breach or other significant cyber incident can severely damage a company's reputation, regardless of its reporting obligations. Proactive cybersecurity measures and transparent communication can help mitigate the negative impact. Future implications: The SEC's actions may pave the way for similar regulations for private companies in the future. Staying ahead of the curve can help you adapt to evolving legal requirements. How to prepare for the new rules: Review and update your incident response plan: Ensure your plan includes clear procedures for identifying, investigating, and reporting cybersecurity incidents within the new timeframe. Establish clear communication protocols: Define who will be responsible for reporting incidents and how information will be communicated internally and to external stakeholders. Invest in cybersecurity training: Educate your employees about cybersecurity best practices and how to identify and report suspicious activity. Seek legal counsel: Consult with an attorney familiar with cybersecurity regulations to ensure your company's compliance with the new rules. Don't wait until it's too late! By actively preparing for the new cyber incident reporting rules, you can protect your company from financial penalties, reputational damage, and the potential for future legal action. Take proactive steps now to ensure your cybersecurity posture is strong and compliant. Additional resources: SEC Cybersecurity Disclosure Rules: https://www.varonis.com/blog/sec-cybersecurity-disclosure-requirements FINRA Cybersecurity Resources: https://www.finra.org/rules-guidance/key-topics/cybersecurity Cybersecurity and Infrastructure Security Agency (CISA): https://www.cisa.gov/ Remember, cybersecurity is a shared responsibility. Let's work together to strengthen our collective defenses and create a more secure digital environment for everyone. Feel free to share your thoughts and questions about the new rules in the comments below!

Why Patching Is Crucial for Cybersecurity? In the ever-evolving realm of cybersecurity, staying ahead of the curve is essential. One of the most critical yet often overlooked aspects of cybersecurity is patching. Patching involves installing software updates that fix vulnerabilities in operating systems, applications, and firmware. These vulnerabilities can be exploited by hackers to gain unauthorized access to systems, steal data, or cause damage. Why is patching so important? There are several compelling reasons why patching should be a top priority for organizations and individuals alike: Vulnerability Reduction: Patches are specifically designed to address known vulnerabilities in software, effectively closing the gaps that hackers could exploit. Threat Mitigation: By promptly implementing patches, you significantly reduce the likelihood of successful cyberattacks. Data Protection: Patching plays a vital role in safeguarding sensitive data from unauthorized access or theft. System Stability: Patches often include bug fixes and stability enhancements, ensuring the smooth operation of your systems. Compliance: Patching is often mandated by industry regulations and standards to maintain compliance. The Risks of Ignoring Patches Failure to prioritize patching can lead to severe consequences: Increased Attack Surface: Unpatched systems become easy targets for hackers, increasing the risk of breaches and data compromises. Regulatory Fines: Non-compliance with patching requirements can result in hefty fines and reputational damage. Business Disruptions: Cyberattacks can cause downtime, disrupt operations, and lead to financial losses. Data Breaches: Exposed vulnerabilities can lead to data breaches, potentially compromising sensitive customer or employee information. How to Prioritize Patching To effectively implement a patching strategy, consider these steps: Establish a Patching Policy: Define clear patching procedures and timelines for your organization. Identify Assets: Create an inventory of all software and systems that require patching. Automate Patching: Utilize automated patching tools to streamline the process and ensure timely updates. Educate Employees: Train employees on the importance of patching and encourage them to report suspected vulnerabilities. Continuous Monitoring: Regularly scan systems for vulnerabilities and prioritize patching those with the highest risk. Patching is not a one-time event; it's an ongoing process that requires continuous vigilance and commitment. By prioritizing patching, you can significantly enhance your cybersecurity posture, protect your data, and minimize the risk of cyberattacks. Remember, a patched system is a protected system.

In the dynamic landscape of cybersecurity and data analytics, organizations are constantly seeking efficient ways to manage their Security Information and Event Management (SIEM) solutions. One compelling option gaining traction is outsourcing the management of Splunk, a leading SIEM platform, to trusted providers like Verizon. Here are ten reasons why this strategic move can prove beneficial for your organization: 1. Expertise and Specialization: Verizon's managed services bring a team of Splunk experts to the table. Their specialized knowledge ensures that your Splunk environment is configured and maintained according to best practices, maximizing its potential. 2. Cost Efficiency: Managing Splunk internally can be resource-intensive. By leveraging Verizon's expertise and infrastructure, organizations can potentially realize cost savings compared to maintaining an in-house team. 3. Focus on Core Competencies: Outsourcing Splunk management allows your organization to concentrate on its core business activities, leaving the intricacies of Splunk administration to the experts. 4. Scalability: Verizon's managed services are equipped to handle scalability requirements. Whether your data volume or user base grows, they can seamlessly adjust resources to ensure optimal performance. 5. 24/7 Monitoring and Support: Enjoy continuous oversight and immediate assistance with Verizon's 24/7 monitoring and support services. This enhances overall security and ensures rapid issue resolution. 6. Security and Compliance: Managed service providers often have robust security practices. Verizon can assist your organization in adhering to compliance requirements, implementing security measures, and providing assistance with compliance reporting. 7. Upgrades and Maintenance: Keep your Splunk environment up-to-date effortlessly. Verizon handles upgrades, patches, and security updates, ensuring your organization benefits from the latest features and remains protected against potential vulnerabilities. 8. Risk Mitigation: Outsourcing Splunk management helps mitigate risks associated with operational disruptions, data breaches, and inadequate system performance. Professional managed services often include comprehensive disaster recovery planning. 9. Global Reach: Verizon's global presence is advantageous for organizations with a distributed or international footprint. Benefit from consistent Splunk management across different regions, ensuring uniformity and compliance with local regulations. 10. Customization and Optimization: Collaborate with Verizon to customize Splunk configurations based on your specific needs and optimize performance over time. This tailored approach enhances the efficiency of your Splunk deployment. In conclusion, entrusting the management of Splunk to Verizon's experienced team offers a strategic solution for organizations aiming to enhance their cybersecurity posture and leverage the full potential of this powerful SIEM platform. Consider exploring this partnership to unlock a new era of efficiency and security for your organization.he body content of your post goes here. To edit this text, click on it and delete this default text and start typing your own or paste your own from a different source.

How to start a SOC on a budget A security operations center (SOC) is a critical part of any organization's cybersecurity posture. A SOC provides 24x7 monitoring of security logs and systems to detect and respond to security threats. However, building and operating a SOC can be expensive, especially for smaller organizations. In this blog post, we will discuss some tips for building and operating a SOC on a budget. 1. Start small You don't need to build a fully staffed, 24x7 SOC overnight. You can start with a small team and add more staff as your needs grow. When you're just getting started, focus on the most important things. Monitor the most important security logs and systems, such as your firewalls, intrusion detection systems, and endpoint security systems. You can add more coverage over time. 2. Use open source tools There are a number of high-quality open source security tools available. This can help to reduce your technology costs. Some popular open source security tools include: Elasticsearch: A distributed search and analytics engine Kibana: A data visualization platform Logstash: A log aggregation and processing pipeline Suricata: A network intrusion detection system OSSEC: A host-based intrusion detection system 3. Consider outsourcing If you don't have the resources to build and operate your own SOC in-house, you can consider outsourcing to a managed security service provider (MSSP). MSSPs can offer you a range of SOC services, including monitoring, management, and incident response. This can be a cost-effective way to get the SOC coverage you need without having to build and operate your own SOC in-house. 4. Automate as much as possible Automation can help you to reduce the cost of your SOC by freeing up your security analysts to focus on more important tasks. Some tasks that can be automated include: Log collection and aggregation Alert triage and prioritization Incident response workflows 5. Use threat intelligence Threat intelligence can help you to identify and prioritize security threats. This can help you to make better use of your limited resources. There are a number of free and commercial threat intelligence feeds available. You can also subscribe to security newsletters and blogs to stay up-to-date on the latest security threats. Conclusion Building and operating a SOC on a budget is not easy, but it is possible. By following the tips above, you can build a SOC that meets your needs and fits your budget. Here are some additional tips: Get buy-in from senior management. It's important to have the support of senior management when building a SOC. This will help you to secure the resources you need. Develop a SOC plan. A SOC plan should outline your goals, objectives, and requirements. This will help you to stay on track and avoid budget overruns. Train your staff. It's important to train your staff on the SOC tools and technologies that you will be using. This will help them to be more effective in their roles. Monitor your SOC performance. It's important to monitor your SOC performance to ensure that it is meeting your needs. You should track metrics such as alert volume, incident response time, and mean time to resolution. By following these tips, you can build and operate a SOC on a budget that will help to protect your organization from security threats.

In August 2023, Clorox, a multinational manufacturer of consumer and professional products, experienced a cyber attack. The attack caused the company to take some systems offline, resulting in production shortages. Clorox warns investors instead of a $150 Million in profits in their 1st quarter they expect to have a loss. Clorox is not the only company to fall victim to a cyber attack in recent years. In fact, cyber attacks are becoming increasingly common and costly. In 2021, the average cost of a cyber attack was $4.69 million, up from $4.24 million in 2020. Cyber attacks can have a devastating impact on businesses of all sizes. They can cause production outages, data breaches, and financial losses. In some cases, cyber attacks can even force businesses to close their doors. That's why it's important for all businesses to have a cybersecurity plan in place. A cybersecurity plan should include policies and procedures for preventing, detecting, and responding to cyber attacks. Businesses should also invest in security tools and technologies to protect their data and systems. Here are a few tips for developing a cybersecurity plan: Conduct a risk assessment to identify your company's vulnerabilities. Implement security policies and procedures that cover all aspects of your business, including IT systems, data, and physical assets. Invest in security tools and technologies, such as firewalls, intrusion detection systems, and antivirus software. Educate your employees about cybersecurity best practices. By taking these steps, you can reduce your risk of becoming a victim of a cyber attack and minimize the damage if one does occur. Here are some additional tips for businesses to protect themselves from cyber attacks: Use strong passwords and two-factor authentication for all accounts. Keep your software up to date. Be careful about what links you click on and what attachments you open. Be wary of phishing emails and other social engineering scams. Have a backup plan in place in case of a cyber attack. Cybersecurity is an ongoing process, and it's important to stay vigilant. By taking the necessary precautions, you can help to protect your business from cyber attacks and the costly consequences that they can bring.

What is Cybersecurity and Why is it Important? Cybersecurity is the practice of protecting systems, networks, and data from digital attacks. It is a critical part of protecting our personal and professional lives in today's digital world. Cyberattacks can come in many forms, including phishing, malware, ransomware, and denial-of-service attacks. These attacks can cause a variety of damage, including financial losses, identity theft, and disruption of critical services. Cybersecurity is important for everyone, but it is especially important for businesses. Businesses store a large amount of sensitive data, such as customer information, financial records, and intellectual property. A cyberattack on a business can have devastating consequences, including financial losses, reputational damage, and even legal liability. Here are some of the reasons why cybersecurity is important: T o protect your personal information. Cybercriminals can steal your personal information, such as your name, address, Social Security number, and credit card number, to commit identity theft. They can also use your personal information to send you spam or phishing emails. To protect your financial assets. Cybercriminals can steal your money by hacking into your bank account or credit card account. They can also use malware to steal your credit card information when you shop online. To protect your privacy. Cybercriminals can use spyware and malware to track your online activity and collect your personal information. They can also use social engineering techniques to trick you into revealing personal information. To protect your devices. Cybercriminals can infect your devices with malware, which can damage your data or steal your personal information. They can also use malware to launch denial-of-service attacks against businesses and organizations. To protect your business. Businesses store a large amount of sensitive data, such as customer information, financial records, and intellectual property. A cyberattack on a business can have devastating consequences, including financial losses, reputational damage, and even legal liability. Here are some tips for improving your cybersecurity: Use strong passwords and enable multi-factor authentication. Strong passwords and multi-factor authentication are two of the most effective ways to protect your accounts from unauthorized access. Be careful about what emails you open and what links you click. Phishing emails are a common way for cybercriminals to steal personal information. Be careful about opening emails from unknown senders, and never click on links in emails unless you are sure they are safe. Keep your software up to date. Software updates often include security patches that can protect your devices from known vulnerabilities. Be careful about what information you share online. Be careful about sharing personal information on social media and other websites. Only share information with people and organizations that you trust. Use a VPN when connecting to public Wi-Fi networks. Public Wi-Fi networks are often unsecured, so it is important to use a VPN when connecting to them. A VPN encrypts your traffic and helps to protect your privacy. By following these tips, you can help to protect yourself from cyber threats and keep your personal and professional information safe.
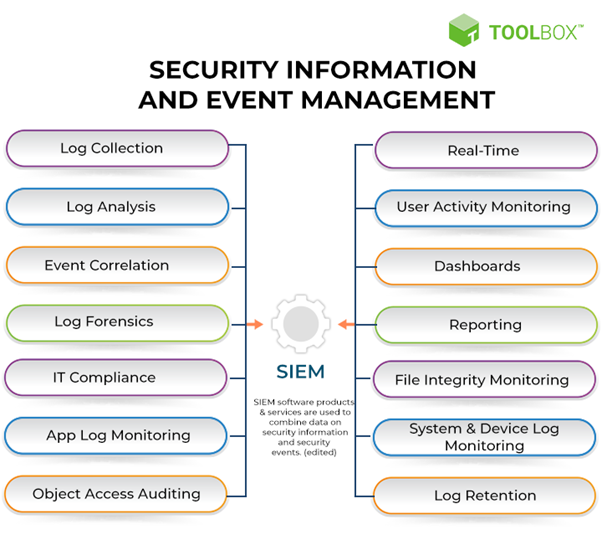
SIEM solutions are powerful tools for security monitoring and incident response, but they can also be complex and time-consuming to set up and manage. The difficulty of setting up a SIEM will vary depending on the specific solution you choose, the size and complexity of your network, and your in-house expertise. However, there are some general challenges that all organizations face when setting up a SIEM: Choosing the right SIEM solution: There are many different SIEM solutions on the market, each with its own strengths and weaknesses. It is important to carefully evaluate your needs and choose a solution that is the right fit for your organization. Collecting data from all relevant sources: SIEM solutions need to collect data from a wide range of sources, including network devices, security appliances, servers, and applications. This can be a complex and challenging task, especially if your network is large and complex. Configuring rules and alerts: SIEM solutions use rules and alerts to identify potential security threats. These rules and alerts need to be carefully configured to avoid false positives and ensure that real threats are detected and investigated. Monitoring and managing the SIEM: SIEM solutions require ongoing monitoring and management to ensure that they are operating correctly and generating accurate alerts. This can be a significant burden on security teams, especially if they are already short-staffed. Given these challenges, it is important to be realistic about the difficulty of setting up and managing a SIEM. If you do not have the in-house expertise, you may want to consider hiring a managed security service provider (MSSP) to help you with this task. Here are some tips for making the SIEM setup process easier: Start small: Don't try to collect and analyze data from all of your systems at once. Start with a small set of critical systems and gradually add more sources over time. Use pre-built rules and alerts: Many SIEM vendors offer pre-built rules and alerts for common security threats. These can save you a lot of time and effort, especially if you are new to SIEM. Get training: There are many training courses and resources available to help you learn how to use and manage SIEM solutions. Taking the time to get trained can help you avoid common mistakes and ensure that you are using your SIEM solution effectively. Overall, setting up and managing a SIEM can be a challenging task, but it is a worthwhile investment for organizations of all sizes. SIEM solutions can help you to improve your security posture and detect and respond to security incidents more quickly and effectively.

A cyber security attack can be devastating for any business, regardless of size or industry. It can cripple your operations, damage your reputation, and cost you millions of dollars. That's why it's so important to have a disaster recovery (DR) plan in place. A DR plan is a set of procedures and policies that outline how your business will respond to and recover from a cyber security attack or other disaster. It should include steps for assessing the damage, containing the threat, restoring your systems and data, and communicating with customers and employees. Here are just a few of the reasons why it's so important to have a DR plan in place: To minimize downtime. A well-crafted DR plan can help you get your business back up and running quickly after a cyber security attack. This is essential for minimizing financial losses and customer dissatisfaction. To protect your data. A DR plan should include steps for backing up your data and storing it in a secure location. This way, you'll be able to restore your data quickly and easily if it is lost or damaged in an attack. To comply with regulations. Many industries have regulations in place that require businesses to have a DR plan in place. If you don't have a DR plan, you could be fined or even shut down. To give your customers and employees peace of mind. Knowing that you have a DR plan in place can give your customers and employees peace of mind knowing that you're prepared to handle any disaster that comes your way. How to create a DR plan Creating a DR plan can be a daunting task, but it's important to remember that it doesn't have to be perfect. The best DR plan is one that is tailored to your specific business needs and that you can update regularly. Here are a few steps to help you get started: Identify your risks. What are the most likely threats to your business? Once you know what you're up against, you can start to develop strategies for mitigating those risks. 2. Assess your assets. What are your most important business assets? This could include your data, your systems, and your reputation. Once you know what you need to protect, you can start to develop a plan for recovering them in the event of a disaster. 3. Develop a recovery plan. This should include steps for restoring your systems and data, communicating with customers and employees, and getting your business back up and running as quickly as possible. 4 .Test your DR plan. Once you have a DR plan in place, it's important to test it regularly to make sure that it works as intended. This will help you identify any areas that need improvement. Conclusion A DR plan is an essential part of any business's cyber security strategy. It can help you minimize downtime, protect your data, comply with regulations, and give your customers and employees peace of mind. If you don't have a DR plan in place, now is the time to create one.



